Notes: Dark web and the onion Routing protocol
Disclaimer
These are just a few quick notes from the videos that have been linked in the headings. Could probably be made into a detailed article but this is all I have right now.
The block quotes or sentences preceeded with ? are questions that pop up in my head while writing these.
Web and internet ——> https://youtu.be/oiR2mvep_nQ
Web is the software that runs on the physical internet Web is just one type of software that runs on the internet Other types include — emails, file transfers (important difference)
Browsers use the web Apps are connected to the internet, not necessarily using web
Two key parts of the web
- Urls / domains
- http server — software that runs on the server that is pointed to by that domain
so web is http?
Deep web ——> https://youtu.be/joxQ_XbsPVw
Bits of the web that we are not allowed to see — by google
4 examples of deep web being different
- Any place behind passwords
- Dynamic content — like search results some site, feeds
- Robot exclusion standards? — robots.txt
- Things that haven’t been linked to
Dark web
Web but built differently There are several dark webs that run on the internet Famous example is tor — onion pages
~ transfer the pages just like the web, just the languages (which I guess means the protocols) are different
Tor ——> https://youtu.be/QRYzre4bf7I
It is an implementation of onion routing
Tor uses 3 intermediate hops
Doesn’t stop anyone from sniffing between nodes
how do key exchanges take place? how is the route decided?
Onion Routing
Create a circuit — the route for the hops ?how? Then do the key exchanges for each node. ?how?
How is onion different from tcp hopping? Or VPNs?
Any message between two nodes can be any point of the hops So the first message is treated the same as the last exit message
Hidden services on dark web ——> https://youtu.be/lVcbq_a5N9I
Services inside the tor network. These services are such that neither the server knows who the client is nor the client knows the server that it is talking to

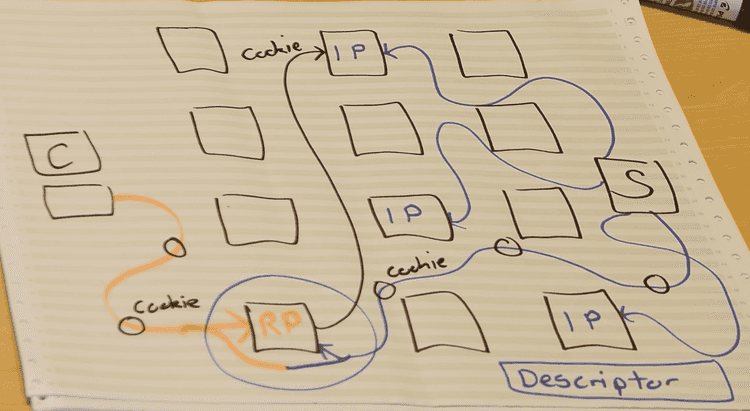
Establishing a connection to a Hidden service
- The hidden service designates 3 random onion routers as introductory points (IP) (all onion routers can be introductory points)
- The server has connections (tor circuits with 3 hops) to these IP
- Then the server creates a descriptor signed by its private key. This descriptor contains the ips of the IP severs in a hash table along with a hash string — which I guess is the onion address
- The user gets this onion address from somewhere and then tries to connect
Connecting to hidden service
- The connection request creates a tor connection ( remember, 3 hops, but this time 2 hops) to a random server server in the tor network. This server is called the rendezvous point (RP)
- This connection request can also contain a random message, like an auth token or password
- The RP then connects to one of the mentioned IP address from the descriptor entry in the shared/distributed hash table.
- It transfers the message sent from the client along with the address of this RP.
- The hidden service has a connection to this IP and so it receives this message
- NOW THE SERVER DECIDES WHETHER IT WANTS TO RESPOND
- ?What if the server denies the request? How does the connection close?
- ?How does congestion control take place?
- If the server does agree to respond, it makes a tor circuit to the RP and then returns the message phrase
- The RP now knows that client that originally sent that message, and so connects that client to this new tor connection and the communication begins
- Note that this connection has more hops than a typical outbound connection request